Azure Tips and Tricks Part 14 - Generate SSH public key to log into Linux VM with Cloud Shell
Intro
Most folks aren’t aware of how powerful the Azure platform really is. As I’ve been presenting topics on Azure, I’ve had many people say, “How did you do that?” So I’ll be documenting my tips and tricks for Azure in these posts.
The Complete List
Click here to view the complete list of Azure Tips and Tricks
Video Available
Generate SSH keys to log into Linux VM with Cloud Shell
We will take what we just learned about Azure Cloud Shell and Storage accounts to connect to create and store a SSH key pair that we’ll use to automatically log into a Linux VM. In my case, we’ll work with a Ubuntu 16.0.4 LTS VM that I originally setup a password for. Instead of typing in a password every time that I wish to connect, I’d prefer to use Cloud Shell storage to generate a public key that I can use to automatically log into the Linux VM without ever typing a password again.
For these instructions, I’ll assume you have a Linux VM already setup and connecting via Cloud Shell.
1.) Log into Azure Cloud Shell and type ssh-keygen -t rsa -b 2048. Accept all default by pressing enter. It has generated a public key that is stored in /home/michael/.ssh/id_rsa.pub. as shown below.
michael@Azure:~/clouddrive$ ssh-keygen -t rsa -b 2048
Generating public/private rsa key pair.
Enter file in which to save the key (/home/michael/.ssh/id_rsa):
Created directory '/home/michael/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/michael/.ssh/id_rsa.
Your public key has been saved in /home/michael/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:FHZVjZfU0zZaXoEvbg37/YUW+02VMIXl6UtUIumpHs0 michael@cc-72f9-63c154d-32136390-qk3bs
The key's randomart image is:
+---[RSA 2048]----+
| o ..ooBB*|
| . o .++*X|
| . . +=*+|
| . o+=o.|
| S +. *+.|
| o E+.=o|
| . .. =.+|
| . . ++|
| =|
+----[SHA256]-----+
michael@Azure:~/clouddrive$
2.) Ensure the key was generated by typing ls -a.
michael@Azure:~$ ls -a
. .. .azure .bash_history .bash_logout .bashrc clouddrive .profile .ssh
3.) Looks good (we see .ssh), we’ll go ahead and copy it to our server with scp ~/.ssh/id_rsa.pub user@ipaddy:
michael@Azure:~$ scp ~/.ssh/id_rsa.pub user@ipaddy:
mbcrump@52.161.31.243's password:
id_rsa.pub 100% 420 0.4KB/s 00:00
4.) SSH to the Linux server with ssh user@ipaddy.
5.) Append the public key to authorized_keys cat id_rsa.pub >> ~/.ssh/authorized_keys and then remove the file with rm id_rsa.pub.
6.) Edit the ssh server configuration file with sudo nano /etc/ssh/sshd_config.
6.1) These entries must be set to yes and they should already be that way by default: RSAAuthentication yes PubkeyAuthentication yes
7.) Reload the configuration with sudo service ssh reload.
8.) Disconnect and try to connect without the need to give the password to the ssh-client ssh user@ipaddy.
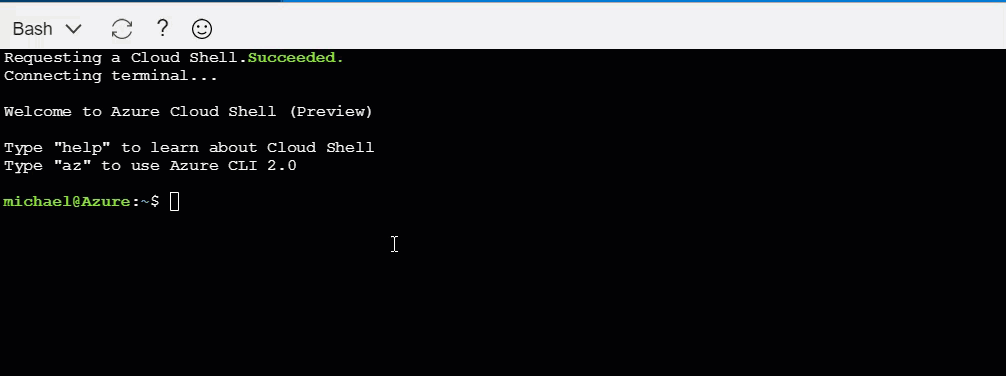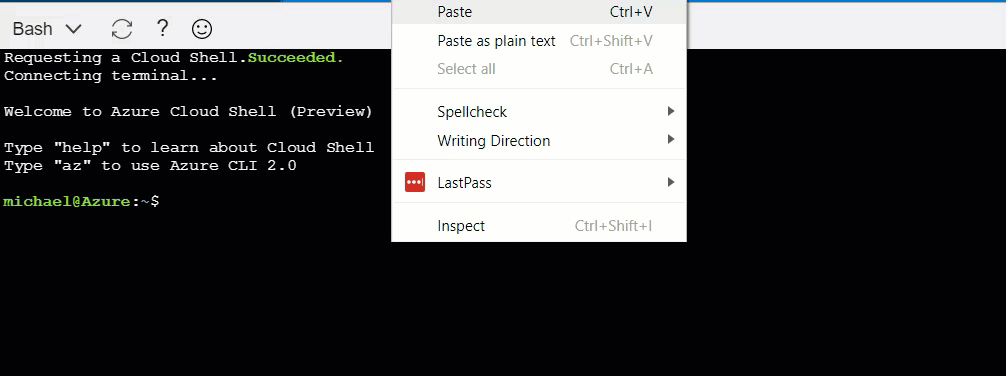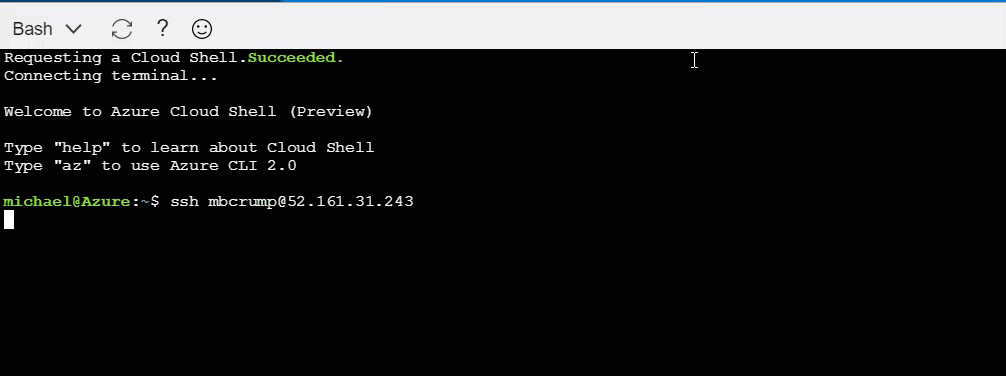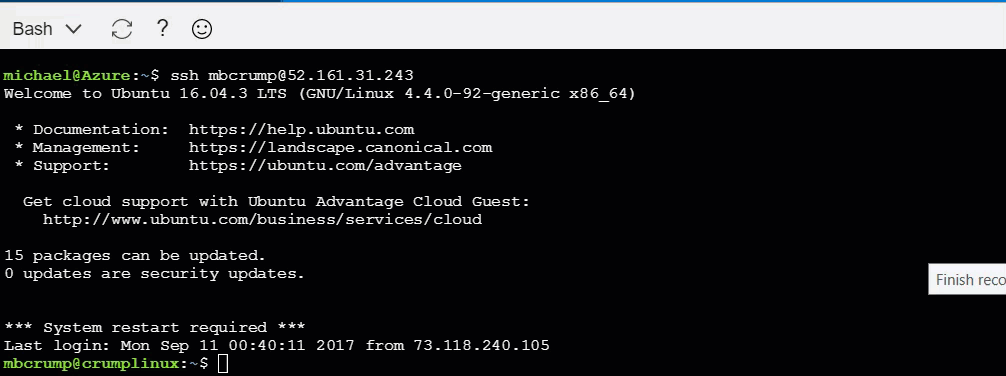
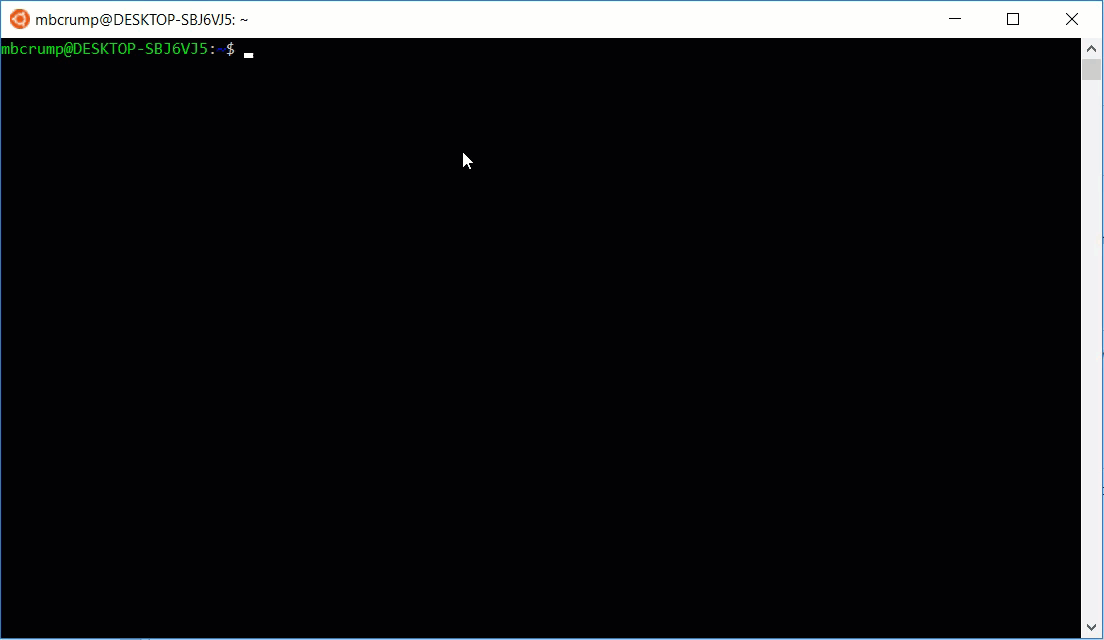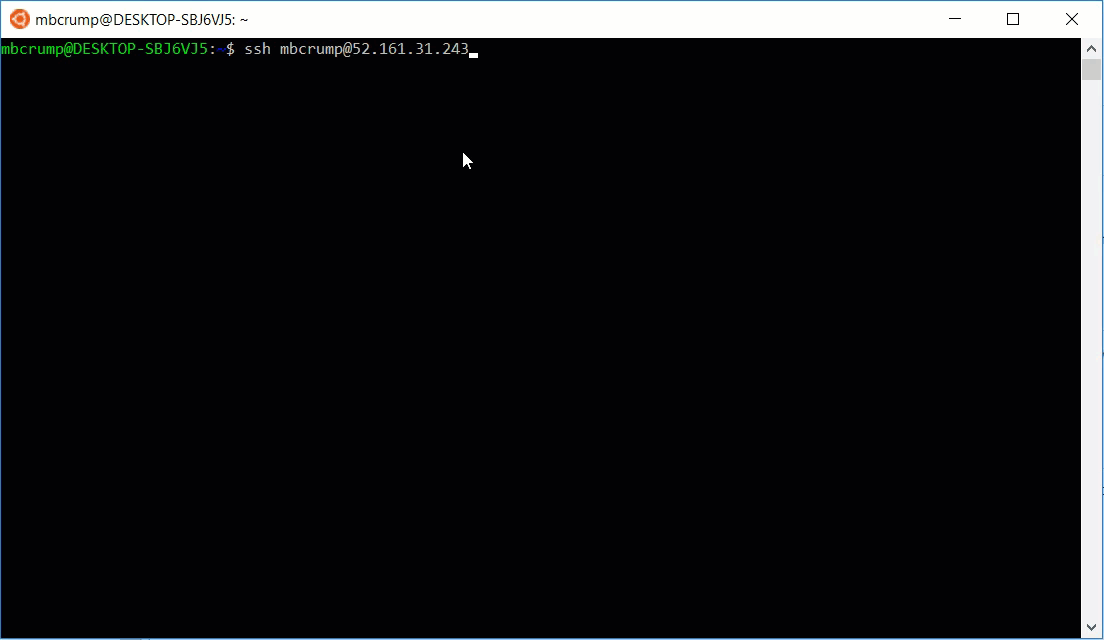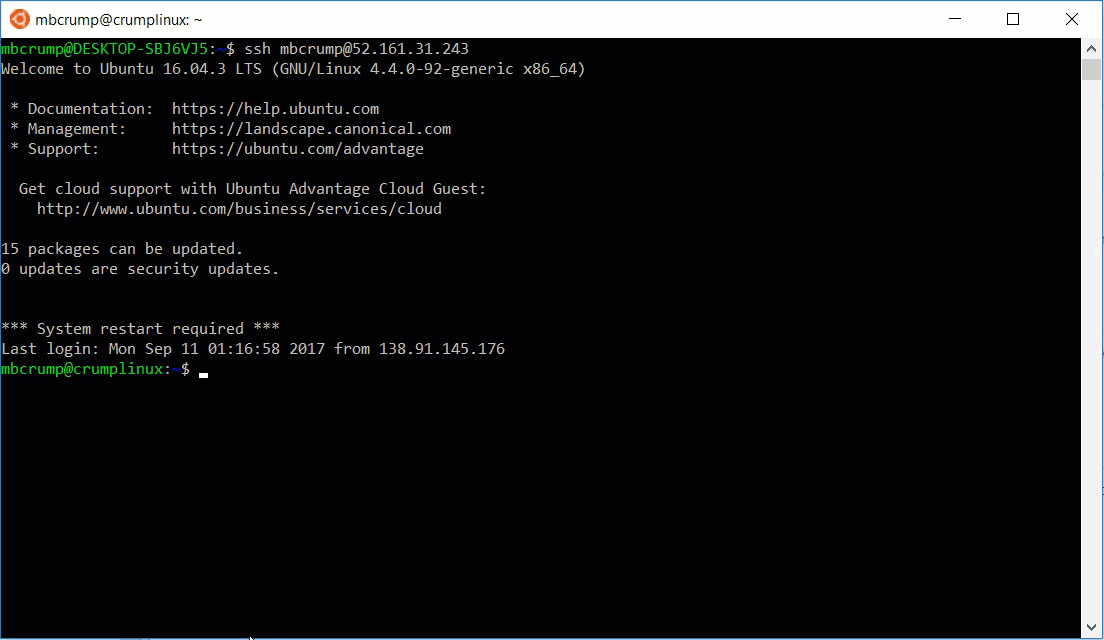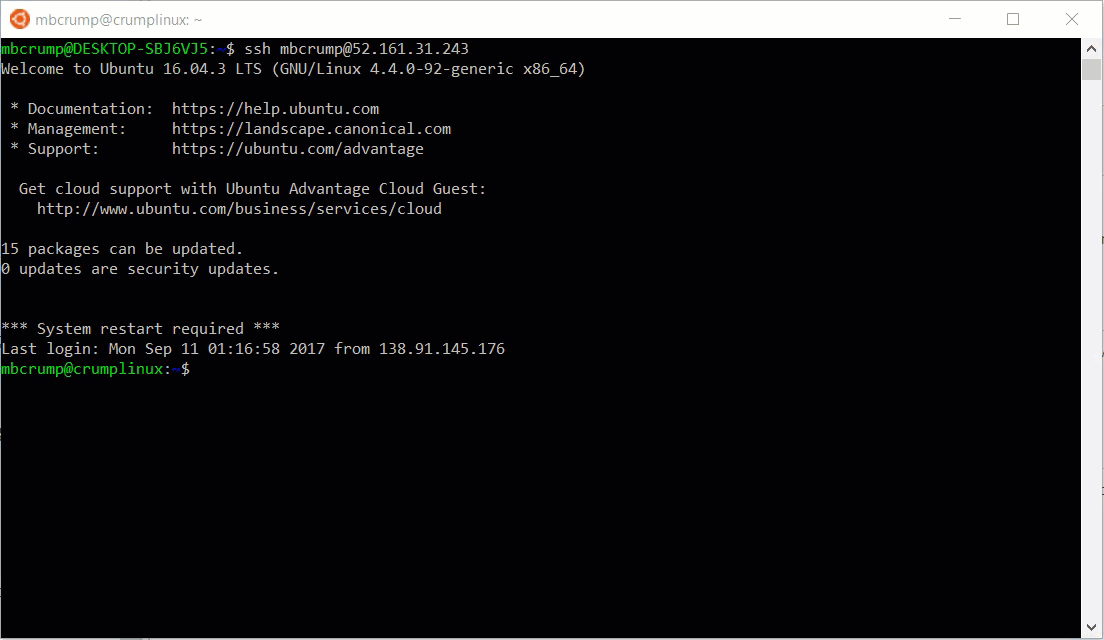
9.) If everything goes as planned, you should see:
michael@Azure:~$ ssh user@ipaddy
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-92-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Get cloud support with Ubuntu Advantage Cloud Guest:
http://www.ubuntu.com/business/services/cloud
15 packages can be updated.
0 updates are security updates.
*** System restart required ***
Last login: Sun Sep 10 23:49:35 2017 from 40.83.147.69
BONUS: If you want to disable the password you previously set on the Linux machine
If you want to disable the password on the Linux machine that you previously set:
1.) SSH back into the machine with ssh user@ipaddy.
2.) Disable password authentication with sudo nano /etc/ssh/sshd_config.
2.1) Ensure the following settings should are set to no:
ChallengeResponseAuthentication no
PasswordAuthentication no
UsePAM no
2.2.) Reload the configuration with sudo service ssh reload
3.) You can see if the password authentication is disabled by logging out and then trying to connect with key file authentication disabled with ssh user@ipaddress -o PubkeyAuthentication=no. You should get “Permission denied”.
BONUS #2: You can easily do the same with BASH on Windows 10
You can have the same goodness that you have with Azure Cloud Shell on your local machine. In my case, I’m using BASH on Windows and can just run steps 1-5 listed above. Boom!
Want more Azure Tips and Tricks?
If you’d like to learn more Azure Tips and Tricks, then follow me on twitter or stay tuned to this blog! I’d also love to hear your tips and tricks for working in Azure, just leave a comment below.

Leave a Comment